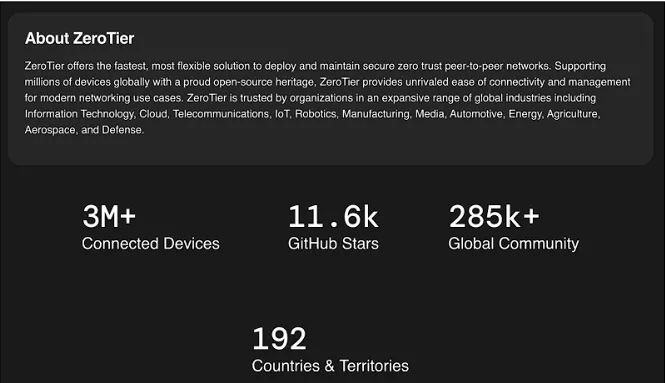
ZeroTier, as its name suggests, is a zero-trust networking solution that securely connects devices anytime, anywhere. Its lightning-fast speed, flexibility, and top-notch security features pave the way for modern, secure, multi-point virtualized networks that transcend physical boundaries.
But what exactly is ZeroTier, and what is it used for? Is it secure and can it be trusted (spoiler alert: yes)? As ZeroTier experts, we figured we’d be in the perfect position to address these questions–and more. We’ll examine its features, explore pros and cons, and verify how ZeroTier compares to competitors.
This article is intended for any person—from a network engineer to a software developer to a CISO—interested in understanding what ZeroTier offers. If you’re actively seeking an advanced solution for modern virtual networking, stay tuned as we dissect this powerful connectivity tool.
ZeroTier Review
ZeroTier is a networking solution gaining traction for seamlessly integrating Virtual Private Network (VPN) and Software-Defined Wide Area Network (SD-WAN) technologies. It’s designed to connect devices across diverse locations as if they were on the same local network. With the increasing need for remote access and security, ZeroTier is a flexible, efficient, and secure option for organizations of all sizes–from SMBs to enterprises.
What is ZeroTier used for?
ZeroTier is a versatile networking tool designed to securely connect devices and networks over the internet. Its vast applications cater to engineers, IT teams, DevOps, embedded systems, and Chief Information Security Officers (CISOs).
Here’s a breakdown of its varied uses:
- IT Teams: For IT professionals, ZeroTier is a blessing. It simplifies network stacks by integrating VPNs, VLANs, and SD-WANs into a single solution. This integration allows IT teams to construct, manage, and monitor any number of remote, on-premise, or cloud networks through a single interface. Moreover, it eases the provision of remote access for an entire team.
- DevOps: Development and operations teams can leverage ZeroTier to build backplane networks spanning multiple cloud providers swiftly. This capability helps save on performance, storage, and bandwidth, as well as facilitates administration and debugging from anywhere. It also provides a secure corporate network overlay and failover layer.
- CISOs: Chief Information Security Officers can leverage ZeroTier’s robust security features, including zero-trust networking and 256-bit end-to-end encryption, to ensure that the organization’s digital assets and communications are secured. This helps in maintaining privacy, ensuring compliance, and protecting against cyber threats.
- Embedded Systems: ZeroTier is also ideal for embedded systems, providing superior network control and functionality. It allows developers to create and manage products or services running on decentralized networks, creating 4G/5G-capable secure networks for any IoT, edge, or embedded device operating on as little as 64MB of RAM.
- Individuals: ZeroTier can also help individuals to access computers, home automation systems, IP cameras, NAS devices, and other home-based devices from anywhere. This remote access comes with the convenience of sharing files or data or playing LAN games—it essentially allows you to manage secure network access for selected users.
ZeroTier Features
ZeroTier’s functionality goes beyond the traditional VPN, enabling users to set up and manage virtual networks easily.
Here are the key features:
- Network Virtualization: ZeroTier’s network virtualization technology is next-generation, allowing you to treat the entire planet as a single data center. By automatically handling the complexities of networking across physical boundaries, we allow users to focus on what matters most. This feature is essential for businesses looking to grow and scale without geographical limitations.
- Peer-to-Peer Networking: ZeroTier establishes direct connections between devices, making communication more efficient. This peer-to-peer architecture ensures minimal latency and that data doesn’t have to pass through unnecessary hoops.
- 256-bit End-to-End Encryption: Security is paramount to any network, and ZeroTier doesn’t disappoint. With scalable, 256-bit end-to-end encryption, we ensure that all data transmitted over the network is secure. This level of encryption is considered one of the strongest, assuring against eavesdropping and data breaches.
- Multi-Cloud Mesh Infrastructure: ZeroTier supports multi-cloud connectivity, enabling a mesh network spanning various cloud providers. This feature is especially useful for DevOps and IT teams working with hybrid cloud environments, as it ensures seamless communication between cloud services.
- Layer 2 Ethernet Emulation: ZeroTier emulates Layer 2 Ethernet with multipath, multicast, and bridging capabilities. This makes it easy to create a network that behaves like a traditional local area network (LAN), but with the ability to connect devices worldwide.
ZeroTier Customers
From small startups to established enterprises, ZeroTier’s secure and flexible networking solutions have proven to be an asset for various teams and industries.
Here’s a closer look at some of our customers and what they have to say:
- Allume Energy: Allume Energy, a company involved in the renewable energy sector, turned to ZeroTier during its early stages of product development. They needed a way to connect their burgeoning IoT product base to their systems easily. Principal Software Engineer at Allume Energy, Peter Boin, stated, “ZeroTier provided an easy and reliable way to achieve that and has been growing with us.”
- SwarmFarm Robotics: Specializing in agricultural robotics, SwarmFarm Robotics relies on ZeroTier as an integral component of its communications stack. Andrew Lipscomb, a Mechatronics Engineer at SwarmFarm Robotics, states, “ZeroTier provides a robust and essential backbone for our communications stack.”
- Loft Orbital: Loft Orbital, a company focusing on making space simple through its innovative space infrastructure, uses ZeroTier to improve interoperability between its offices in the United States and France. Brunston Poon, a Software Engineer at Loft Orbital, shared, “It connects our engineers to key resources quickly and easily, which allows our team to focus on making space simple.”
ZeroTier Pros
ZeroTier boasts various features designed to make virtual networking effortless and secure. It combines the capabilities of traditional VPNs with the flexibility and scalability of software-defined networks.
Let’s take a look at some of the key benefits of using ZeroTier:
- Cross-Platform Support: ZeroTier supports various platforms, including Windows, macOS, Linux, iOS, Android, and more. This flexibility makes it easy to integrate almost any device into a ZeroTier network, regardless of the operating system.
- Highly Secure: With 256-bit end-to-end encryption and a zero-trust security model, ZeroTier ensures that the data transmitted across its networks is protected against unauthorized access and eavesdropping.
- Global Connectivity: ZeroTier allows users to create virtual networks that span the globe. This is particularly advantageous for businesses with teams in multiple locations, as it facilitates seamless collaboration regardless of geographical location.
- Scalability: ZeroTier networks can be scaled up or down easily. Whether you need to connect two devices or thousands, ZeroTier can accommodate your needs without significant changes to the network configuration.
- Ease of Use: One of ZeroTier’s standout features is its user-friendliness. Setting up a network can be done in minutes, and managing it through the centralized interface is intuitive, even for those with limited networking knowledge.
- Community and Documentation: ZeroTier has a community forum and comprehensive documentation, including a knowledge base. This ensures users have access to the information and support they need to maximize ZeroTier.
- Developer-Friendly: ZeroTier’s SDK is available for developers who want to embed high–performance networking into their applications. This adds value to products and services, especially IoT and cloud-based applications.
ZeroTier Cons
Like any technology, ZeroTier can have limitations–and we’ll be honest about that. Here’s where we’re working to improve our services right now:
- Coordination Through Central Servers: Currently, ZeroTier relies on central servers to coordinate nodes within the network. While no data actually passes through these servers, we understand that some users may have concerns about relying on a third-party service for network coordination. However, this centralized coordination aids in efficient network management and helps to establish connections between nodes, especially in complex network configurations. Our team is exploring ways to offer more flexibility while maintaining the simplicity and effectiveness of our system.
- No Native Internet Traffic Routing: As of now, our platform doesn’t natively support routing all internet traffic through the virtual network—a feature some users might expect from a VPN solution. However, this design decision gives our users greater control over their network traffic, reducing unnecessary bandwidth usage and potentially increasing network performance. Nonetheless, we recognize the demand for integrated traffic routing, and we are diligently working on methods to incorporate this functionality in a manner that complements our existing features and user needs.
ZeroTier Pricing
We offer a range of pricing options to make networking accessible for every business.
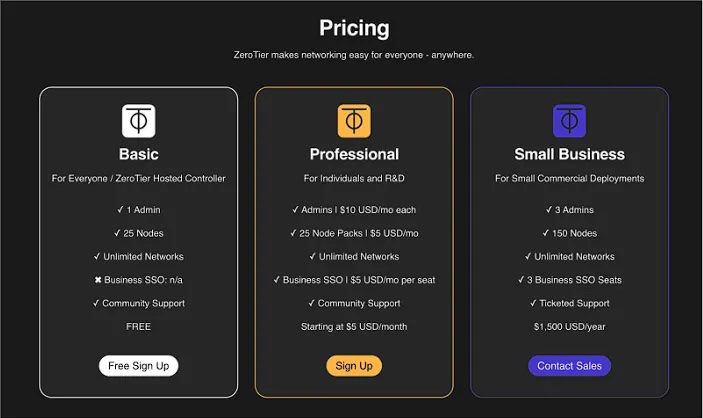
Basic Plan (ZeroTier Hosted Controller)
Target Audience: For Everyone.
Cost: Free
Features:
- 1 Admin
- 25 Nodes
- Unlimited Networks
- Community Support
- No Business Single Sign-On (SSO)
Professional Plan (For Individuals and R&D)
Target Audience: Licensed Only For Individuals and Testing.
Cost: Starting at $5 USD/month
Features:
- Admins at $10 USD/month Each
- 25-Node Packs at $5 USD/month
- Unlimited Networks
- Business SSO at $5 USD/month Per Seat
- Community Support
Business Plan (For Licensed Commercial Deployments)
Target Audience: Businesses with more extensive networking requirements.
Cost: Contact Sales
**Use Cases: **
- IoT
- SD-WAN
- VPN
- Remote Monitoring and Management
Enterprise Plan
Target Audience: Large enterprises with high-volume VPN, IoT, edge, embedded networking, multi & hybrid cloud, and Infrastructure as Code (IaC) requirements.
Cost: Contact Sales for customized pricing.
**Features: **Customizable based on the specific needs of the enterprise, including the potential for more nodes, admins, networks, and support options.
Service Providers Plan
Target Audience: Hardware and software companies, Managed Service Providers (MSPs), Resellers, and Systems Integrators.
Cost: Contact Sales for customized pricing.
Features: Customized to suit integration or embedding of the ZeroTier platform within service offerings and for enterprise-facing channels.
ZeroTier FAQs: Everything You Need to Know
In this section, we aim to answer people’s common questions about ZeroTier, from its functionality as a VPN to security concerns. This information will help you decide whether ZeroTier suits your networking needs.
Does ZeroTier work as a VPN?
Yes, ZeroTier does work as a VPN–but with a twist. Traditional VPNs (Virtual Private Networks) primarily focus on securing your internet connection by routing it through a server, which can be used to access resources on a remote network or hide your IP address. We take this a step further by combining the capabilities of a VPN with the flexibility and functionality of SD-WAN (Software-Defined Wide Area Network).
Is ZeroTier a virus?
No, ZeroTier is not a virus. It’s a legitimate and reputable software used for creating virtual networks that offers scalable security. However, as with any software, it’s important to be cautious and only download ZeroTier from our official website.
Does ZeroTier encrypt traffic?
Yes, ZeroTier does encrypt traffic. It employs a zero-trust networking model and uses strong 256-bit end-to-end encryption to secure the data transmitted across its virtual networks. This level of encryption is comparable to what is used in most traditional VPNs and is highly secure. The encryption ensures that even if data is intercepted while being transmitted between devices on the ZeroTier network, it cannot be easily deciphered or tampered with.
ZeroTier also uses certificates and keys to authenticate devices before they join the network. Only verified devices with the correct credentials can become part of your ZeroTier network.
Is ZeroTier free?
Yes, ZeroTier does offer a free tier known as the Basic Plan. This plan is suited for general users and small-scale projects. This plan is particularly useful for individuals who want to experience ZeroTier’s capabilities without financial commitment. It’s also great for small projects that do not require multiple nodes or advanced features.
However, for those who need more features or have more extensive networking requirements, we offer additional paid plans. These plans come with more features and support options and are priced accordingly and are ideal for SMBs and enterprises launching or securing an app, scaling their business in a new location, managing remote access for users, and more.
Is ZeroTier safe? Can ZeroTier be trusted?
Yes, ZeroTier is safe and can be trusted. In terms of security features, ZeroTier employs 256-bit end-to-end encryption to secure data transmitted across its networks. Additionally, ZeroTier uses a zero-trust networking model, meaning the platform doesn’t automatically trust any entity within the network. Devices are authenticated before they join the network, which reduces the risk of unauthorized access.
Regarding trust, it’s also worth noting that we’re transparent about our operations and provide detailed documentation through our website and knowledge base.
However, like any software, ZeroTier’s safety can also depend on how it is configured and used. It’s crucial to follow best practices for security, such as regularly updating the software, using strong authentication methods, and monitoring network traffic. It’s also important to consider the source of the software; downloading ZeroTier from our official website or a verified source ensures that you’re getting untampered software.
What are the security issues with ZeroTier?
Like any software or networking solution, ZeroTier is not immune to potential security issues if it’s not set up or used correctly. It’s important to know the following risks and understand how to mitigate them:
- Misconfiguration: One of the most common security issues with networking software arises from misconfiguration. Inadvertently leaving ports open, using weak authentication methods, or failing to set network access controls properly can expose the network to unauthorized access.
- Outdated Software: Running an outdated version of ZeroTier can leave your network vulnerable to exploits that have been patched in newer versions. It’s important to check for updates regularly and apply them right away.
- Dependence on End-User Security Practices: ZeroTier’s security also depends on the security practices of the users and devices connected to the network. If a device connected to your ZeroTier network is compromised, it can expose the entire network to risks.
- Software Vulnerability Patches: Like any software, ZeroTier may have unknown vulnerabilities that malicious actors could try to exploit. While we employ strong encryption and a zero-trust model, staying informed about any new security advisories or patches is essential.
- Third-Party Access: If you use ZeroTier’s networks to grant third-party access to certain resources, a risk is involved if the third party’s security is compromised. You should be cautious and selective about who has access to your network.
To mitigate these security issues, it’s advisable to follow these best practices:
- Regularly update ZeroTier to the latest version.
- Configure network settings securely, following the recommendations in ZeroTier’s documentation.
- Educate network users on security practices.
- Monitor network traffic for any unusual activity.
- Limit access to the network to only those who need it and regularly review access controls.
Is ZeroTier legit?
Yes, ZeroTier is a legitimate and reputable networking software. Here are a few factors that demonstrate why:
- Established Company: ZeroTier, Inc., the company behind ZeroTier, is an established company in the networking space. We have been around for several years and are known for providing virtual network solutions.
- **Wide Adoption: **ZeroTier is used by a broad spectrum of users, from individuals to businesses and developers. Its adoption by reputable companies and positive user testimonials adds to our legitimacy.
- Open Source: Parts of ZeroTier’s code are open, meaning the community and experts can review the code. This openness is often considered a positive attribute in verifying the legitimacy of our software.
- Active Community: ZeroTier has an extremely active community of users and developers. In fact, many of our new clients and customers come from word-of-mouth referrals through our community.
- Continuous Development and Support: At ZeroTier, we believe in the power of continuous development and dedicated customer support. This commitment is reflected in our regular updates that aim to enhance our product’s functionality and usability. We also place high importance on providing robust support options for our customers, with comprehensive resources including a detailed knowledge base, community support forums, and for professional and small business packages, we offer ticketed support.
Get Started with ZeroTier
Whether you’re a CISO tasked with ensuring secure connectivity across your organization’s infrastructure, an IT team managing complex network infrastructure, or a developer building next-generation applications, ZeroTier offers a wide range of features to suit your needs. Its robust security measures, ease of use, and various pricing options make it a compelling choice for many.
To begin your journey with ZeroTier:
- Visit the Official Website: Navigate to ZeroTier’s official website. Ensure that you are visiting the legitimate site to avoid any counterfeit software.
- Sign Up for an Account: Create an account by providing the required information. This will also help you manage your networks and settings from a centralized dashboard.
- Choose a Plan: ZeroTier offers various plans, including a free tier. Choose the one that best fits your needs.
- Download the Install: Download the ZeroTier client for your operating system and install it. Keep your software updated to the latest version for security and performance enhancements.
- Create a Network: Once logged into the ZeroTier interface, create a new virtual network.
- Invite Devices and Users: Invite devices and users to your network by sharing the network ID or through the ZeroTier interface. Make sure to set the appropriate permissions for each user.
- Configure Network Settings: Configure your network settings according to your requirements. Consult the ZeroTier documentation and knowledge base for best practices.
- Verify Connections: After setup, verify that all devices and users are connected securely and that they can communicate within the network.
- Monitor and Maintain: Regularly monitor your network for any unusual activity, and keep abreast of any updates or security advisories posted by ZeroTier.
Now you are ready to harness the power of ZeroTier for your virtual networking needs. ZeroTier can be a transformative tool for connecting and communicating across devices and locations, whether for personal use or your business.
