The internet began as a simple, open network where every device could reach every other directly. Researchers and engineers built new applications on top of that open foundation, and collaboration thrived.
Over time, new layers of protection fractured that simplicity. Firewalls, NAT gateways, and corporate perimeters made it harder for devices to reach one another directly. What began as a peer-to-peer web of trusted connections turned into a maze of intermediaries. This expanding complexity also introduced more weak spots and an ever-growing attack surface, increasing the risk and maintenance burden for network operators.
Most of the internet’s traffic now flows through centralized providers and cloud systems that decide who can connect, how, and when. That shift created new single points of failure, breaking the original peer-to-peer design. Networks became harder to manage, slower to adapt, and more dependent on static infrastructure.
ZeroTier was built to unbreak that model: to restore the simplicity of direct, secure, peer-to-peer connection across the modern internet. It was designed to overcome the barriers introduced by NAT, firewalls, and IPv4 exhaustion while maintaining the open, end-to-end principles that defined the early internet. By rebuilding these fundamentals on top of modern encryption and intelligent routing, ZeroTier makes it possible to connect devices anywhere in the world as if they were still part of one continuous network.
The foundation: virtual ethernet everywhere
ZeroTier creates a virtual ethernet network that runs on top of any existing IP network. Every device, server, or container you connect becomes part of a shared virtual LAN that behaves as if it were local.
Unlike traditional VPNs that route all traffic through a central hub, ZeroTier lets devices communicate directly whenever possible. This overlay recreates the internet’s original end-to-end behavior, letting your devices connect securely and efficiently regardless of where they live or who owns the underlying network.
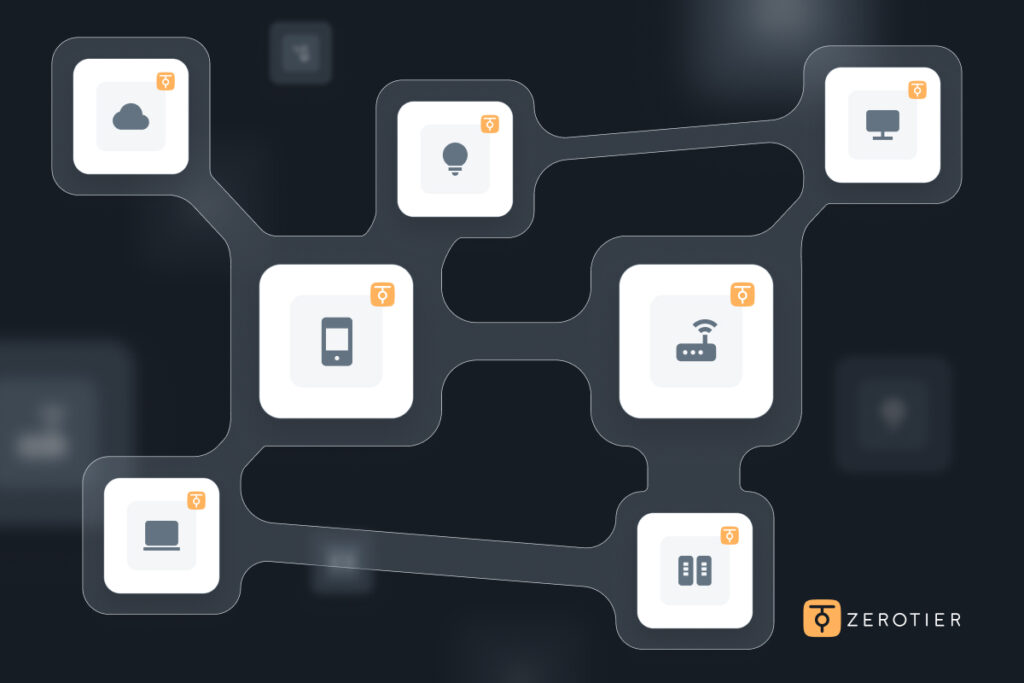
Why hub-and-spoke VPNs fall short
Most VPNs still depend on a central concentrator. Every client connects through a single point, and all data must travel through it. That works for small networks but collapses under scale.
Traffic between two endpoints often detours through distant infrastructure, adding latency, and failure points. Depending on the network design, a concentrator VPN can be a single point of failure for large swaths of remote workers or devices. Furthermore, security models relying on legacy VPNs can be at increased risk under an “inside is trusted” policy that is often found in older hub-and-spoke topologies. Hub-and-spoke designs also force administrators to manage static IPs, firewall rules, and key distribution. Each change requires manual coordination, which compounds as networks expand across clouds and geographies. This can be particularly tricky in multi-cloud environments or with high IoT, IIoT, OT, and edge computing use cases.
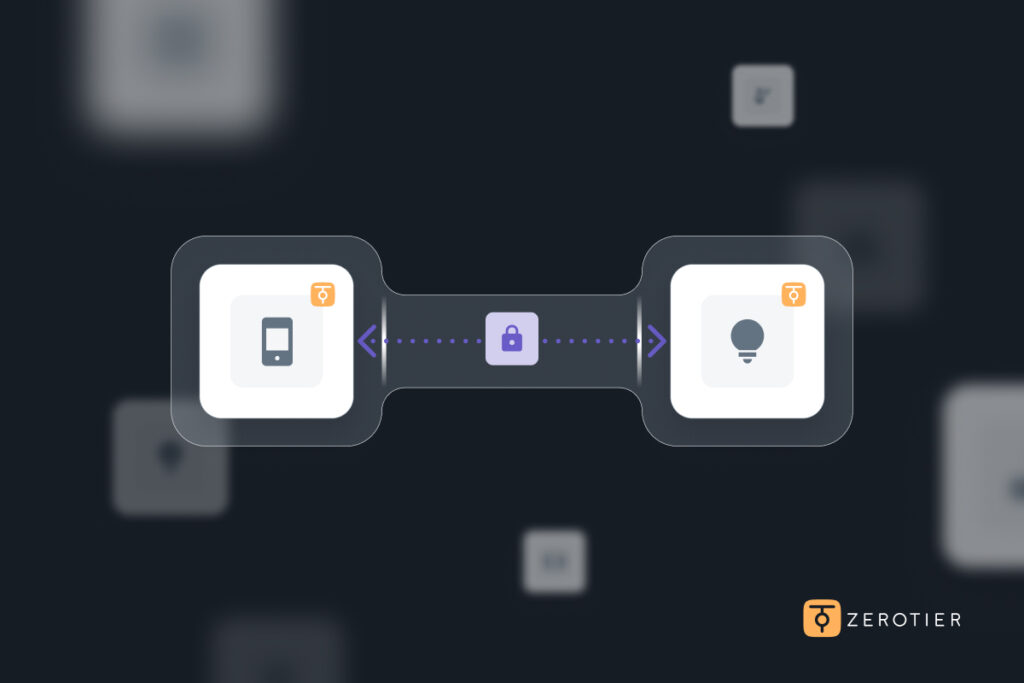
Enter ZeroTier: peer-to-peer overlay for a broken Internet
ZeroTier replaces fragile tunnels with a distributed software-defined overlay. Each device runs a lightweight agent that handles cryptographic identity, NAT traversal, and virtual network configuration automatically. Devices communicate with a controller to exchange membership data and security policies, but data flows directly between peers whenever possible. Policy remains centralized. Traffic does not.
Cryptographic identity, not static IPs
In traditional networks, identity depends on where a device sits. IP addresses define access, and moving a system between subnets means changing its identity. ZeroTier replaces this with cryptographic identity. Each device generates a unique keypair that defines who it is. Controllers distribute public keys and authorize membership, while private keys never leave the device.
Trust becomes portable and self-verifiable. Devices move freely between networks, clouds, and providers without losing their identity. You no longer need static IPs or complex DNS mapping to stay securely connected.
For example, a laptop running ZeroTier can move from office Wi-Fi to a mobile hotspot to a home network without losing connectivity or needing to reconfigure IP settings. It keeps its identity, maintains encrypted connections, and remains reachable wherever it goes. This approach eliminates configuration drift, avoids IP conflicts, and removes the need for manual key management, all common pain points in traditional networking.
Furthermore, ZeroTier’s encryption is accelerated on most hardware, minimizing any added latency to peer traffic. We call this data-in-transit-security (DITS). The platform is by design cryptographically secure that even ZeroTier cannot see end-user data. Master controllers and root servers merely help peers find each other, but cannot decrypt any data flowing over them because they never see anyone’s private keys.
Making network connections easy
ZeroTier networks adapt automatically. Devices can appear, disappear, or move physically or logically without breaking connectivity. The overlay forms new paths in real-time as network conditions change. This ephemeral architecture is ideal for mobile, containerized, and IoT deployments. Devices can securely join and leave as needed. The network heals itself and keeps running smoothly, no matter how the underlying internet behaves.
This model also supports the way modern infrastructure operates. In cloud, edge, and containerized environments, workloads are constantly spun up and down. ZeroTier’s design embraces this fluidity by allowing identities and connections to exist only as long as they’re needed. Once a device or container is destroyed, its credentials become irrelevant, naturally reducing the attack surface and improving operational security.
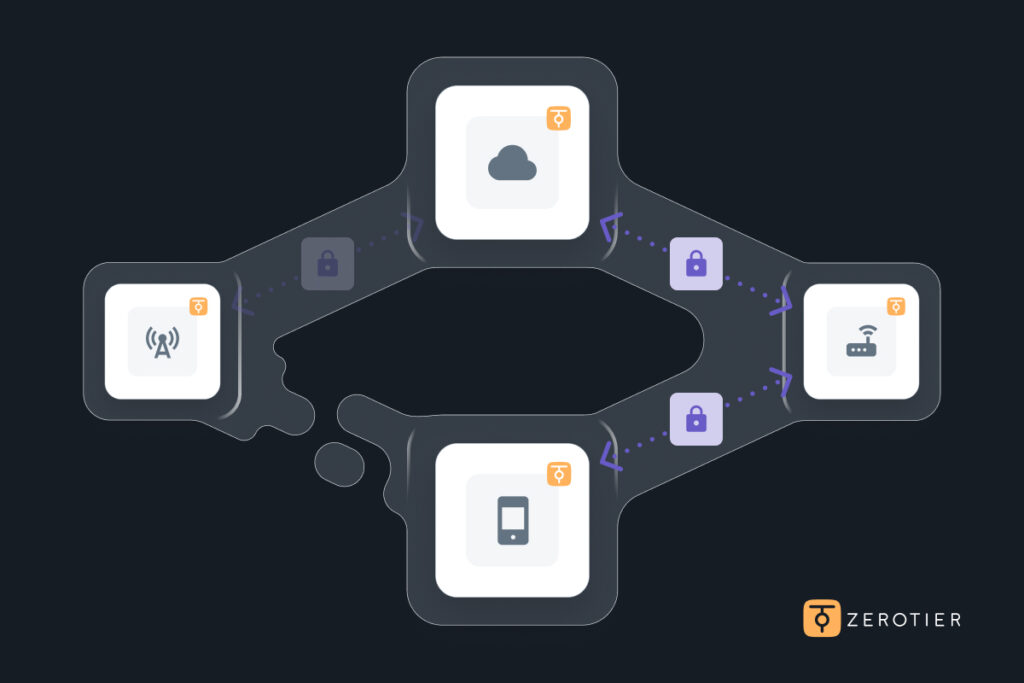
Flattening the network: any device can be a server
ZeroTier erases the old client-server divide. Any device can host a service or share data directly with another peer.
The controller defines access policy but doesn’t route or inspect traffic. This flattens the network and removes bottlenecks. You no longer need concentrators, edge gateways, or multiple layers of translation. Instead, one consistent policy fabric governs everything, everywhere.
Imagine a developer running a local test server on a laptop that instantly becomes reachable by teammates around the world without port forwarding or static routes. Or a small cluster of IoT sensors exchanging data directly with each other without cloud mediation. Flattening the network doesn’t just simplify management, it restores the flexibility and collaboration that the internet was originally built for.
Real-world routing efficiency and high performance
When a direct route exists, ZeroTier uses it. When it doesn’t, traffic relays automatically through the nearest available path. This hybrid model combines centralized intelligence with distributed data flow, improving performance and resilience. Mobile devices that are switching between different physical layer connection options often show large jumps in performance, by both routing efficiency and rapid multi-pathing capabilities.
Because ZeroTier operates at the virtual ethernet layer, it works seamlessly with existing applications and protocols. Your software behaves as if everything were on the same LAN, even when devices are scattered across the world. You can even adjust your own traffic down to the device level with ZeroTier’s flow rules.
Logging, visibility, and compliance
Peer-to-peer doesn’t mean invisible. Each device can report connection metadata to centralized systems for monitoring, auditing, or compliance.
You maintain full visibility without forcing all traffic through an inspection point. This approach brings modern observability to a distributed environment, where trust is based on verification instead of blind openness.
The ZeroTier advantage
- Peer-to-peer overlay: Restores the internet’s original design.
- Cryptographic identity: Trust based on math, not geography.
- Unlimited scale: Join, leave, and scale instantly.
- Flattened architecture: Any device can be a peer or server.
- Central control, distributed data paths: Governance without choke points.
- Hardware agnostic: Old, new, server, mobile, laptop, and IoT device — all work and can extend the life of existing hardware.
- Virtual ethernet: Seamless compatibility with existing systems. ZeroTier lets you build private networks that just work. It’s secure, scalable, and simple enough to deploy in minutes.
- Purpose-built and extensible: ZeroTier’s entire platform is fully controlled and not limited by OSS foundation.
The future: unbreaking the internet
The internet broke when complexity replaced connection. Every layer added to protect it made it less direct, less open, and less efficient.
We believe there’s a better way. By combining cryptographic identity with peer-to-peer simplicity, ZeroTier brings the internet back to what it was meant to be: a trusted fabric that connects everything, everywhere, without getting in the way.
The future of networking depends on returning to those fundamentals. As organizations adopt decentralized infrastructure, edge computing, and even quantum-safe encryption, the ability to connect securely without intermediaries becomes essential. ZeroTier’s approach proves that simplicity and security can coexist, and that rebuilding trust at the network layer is the foundation for whatever comes next.
Ready to learn how ZeroTier can simplify and secure your connectivity? Request a demo today.

