Firewalls and policy engines exist for a simple reason: the internet doesn’t provide trust by default. It was designed to move packets reliably, not to verify identity, intent, or safety. Any reachable system can be scanned or attacked, and any exposed service becomes part of the global attack surface. Firewalls reduce that risk by deciding which traffic is allowed to exist at all, shrinking exposure and narrowing the blast radius before problems spread.
We’re excited to officially announce the roll out of ZeroTier’s latest release for Central, which introduces ”flow rules” in template form. Flow rules themselves aren’t new to ZeroTier. They’ve existed for years as an element of ZeroTier One and have quietly powered some of the most sophisticated ZeroTier deployments. What’s new is bringing that capability forward into Central’s UI, making a proven, powerful policy engine easier to use, easier to reason about, and available to a much broader set of users. If you’ve spent years building and maintaining rulesets around static perimeters, IP ranges, and edge-bound appliances, flow rules are a deliberate reset. They’re ZeroTier’s native policy model, built for decentralized, zero-trust networks where location fades into the background and identity takes over.
What Are Flow Rules?
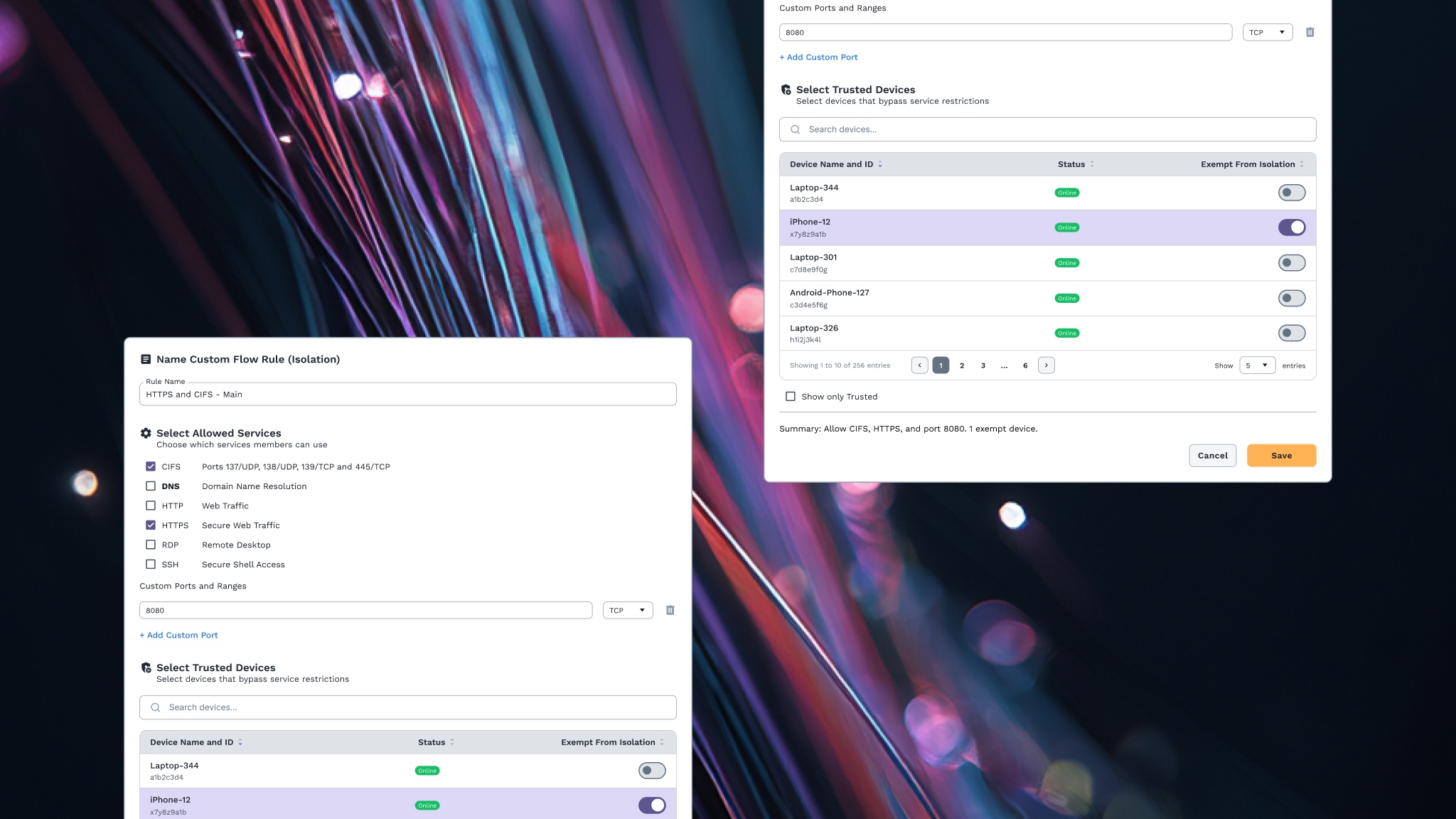
Before we break it down further, let’s first answer: what exactly are flow rules? Flow rules define how devices and services can communicate on a ZeroTier network. Rules are enforced locally on each device, not through a central firewall. By default, all traffic is permitted within whatever existing traffic and rules allow in the macro environment. Flow rules are used to restrict, limit, or permit communication as needed. Additionally, by virtue of what they do, they offer many additional benefits like flexible network topology configurations.
In practice, these benefits appear most clearly in how flow rules can handle topology, integration, and control. Because they operate at the overlay, rather than the underlying infrastructure, flow rules make flexible designs like hub and spoke practical even when environments span multiple clouds, providers, and physical networks. A hub can live in one environment, spokes in another, and endpoints anywhere else, with the same policy enforced consistently across all of it.
Flow rules are also complementary to existing security controls. They don’t override upstream firewalls, security groups, or routing decisions. Instead, they apply an additional, identity-aware policy layer once traffic is already permitted to exist. That makes it safe to introduce incrementally, without re-architecting or weakening what’s already in place. Within that layer, flow rules provide fine-grained control over traffic, with policies that can match on protocol, port, IP version, direction, and identity-based tags. The result is a policy model that’s precise enough to enforce least privilege, yet flexible enough to move with the network as it changes.
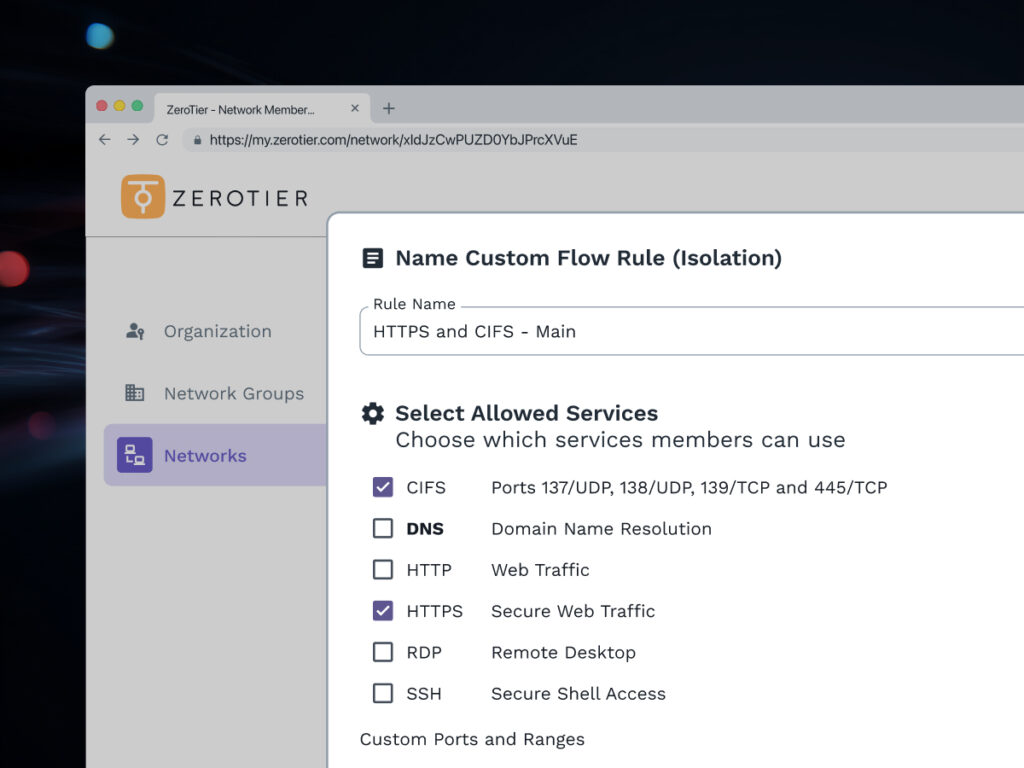
In ZeroTier’s new Central, flow rules are now delivered through UI-based templates. Our first template release for network isolation, covers the widest array of use cases seen in ZeroTier deployment. It offers a focused set of policy controls that define how traffic moves within a network. It’s a menu of settings rather than a single switch or a deep scripting interface, providing a clear starting point with room to customize. This template is the first of many, setting the foundation for additional templates, and enhanced full scripting capabilities, that make powerful network policies easier to deploy as Central continues to evolve.
What Are the Benefits of Flow Rules?
In practice, flow rules move policy enforcement off a centralized firewall and onto every device in the network. Instead of inspecting traffic at a single boundary, rules are defined once in Central and distributed cryptographically to each node, where they’re evaluated locally on every packet. Enforcement happens at the source, in real time, without relying on a shared choke point. The result is policy that’s consistent everywhere, resilient by design, and better suited to how modern, distributed infrastructure actually operates.
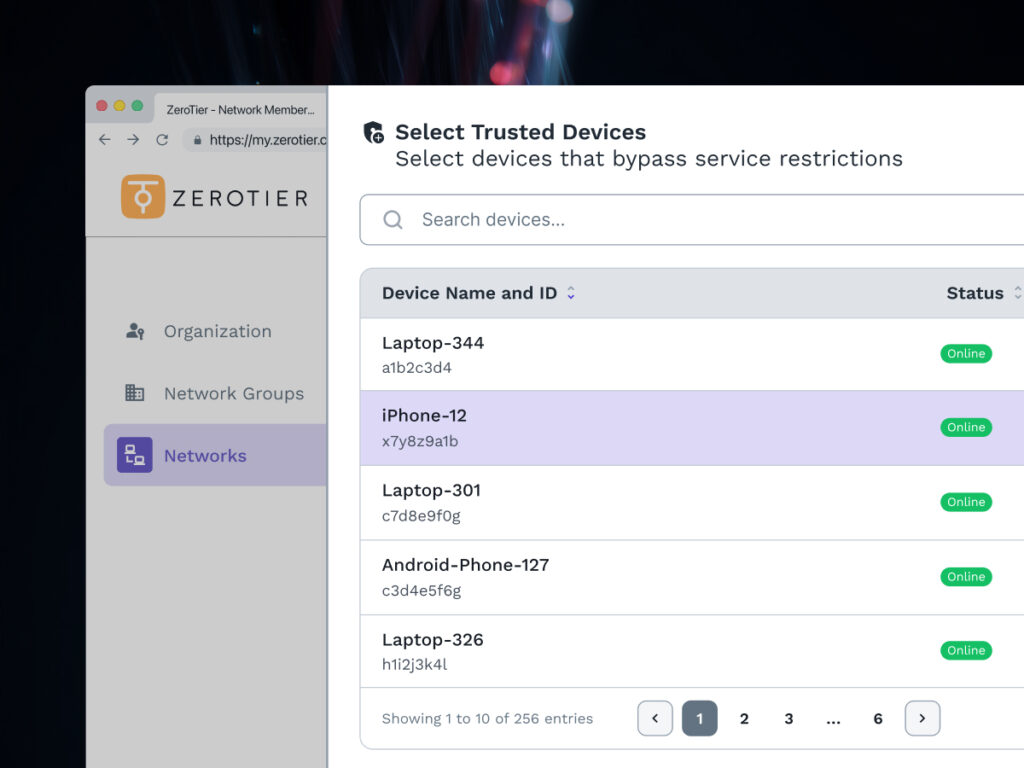
Because flow rules are identity-aware, they don’t depend on brittle constructs like fixed IP addresses or centralized choke points. Traffic can be matched on protocol, port, direction, and identity-based tags that describe what a device is and what it’s allowed to do. That means you can express intent directly. For example, you can permit telemetry from devices tagged as drones to devices tagged as controllers, without caring where those devices are physically located or how often they move. Policy follows the workload, not the rack.
Enforcement is stateful and local. When traffic is allowed, replies are handled automatically without additional configuration. When traffic is denied, it never leaves the originating device. There’s no hairpinning through a remote firewall and no dependency on a central appliance staying online to make a decision. This sharply reduces attack surface and limits lateral movement, even if a device is compromised. From an operational standpoint, it also removes a class of failure modes that mid-level IT teams spend far too much time mitigating.
Compared to legacy firewalls, flow rules are not a feature bolted onto an old model. They’re a policy engine designed around mobility, peer-to-peer communication, and evolving networking needs. They assume devices come and go, workloads shift, and networks span clouds, data centers, and the physical world. Traditional firewalls still matter, of course, especially for north-south traffic and compliance boundaries, but they were never built to enforce least privilege everywhere, all at once.
Flow rules make zero trust practical because they enforce it where it counts: at the endpoint, on every packet, all the time. With this early-February release of Central, ZeroTier customers get a clearer, more scalable way to express intent and enforce policy across decentralized environments. It’s not about replacing everything you already run. It’s about finally having a policy engine that matches how you want your network to operate.
This release is just the beginning. Next up are additional templates and more customization options, making it even easier to model real-world architectures and enforce intent at scale. As ZeroTier continues to evolve Central, our goal remains the same: providing teams with practical tools to build defense-grade, secure, decentralized networks without forcing modern infrastructure into outdated patterns.
Want to learn how ZeroTier’s resilient, identity-first networking limits access by design? Request a demo today.
Want a deeper breakdown of the terminology? Our networking and cybersecurity glossary has you covered.